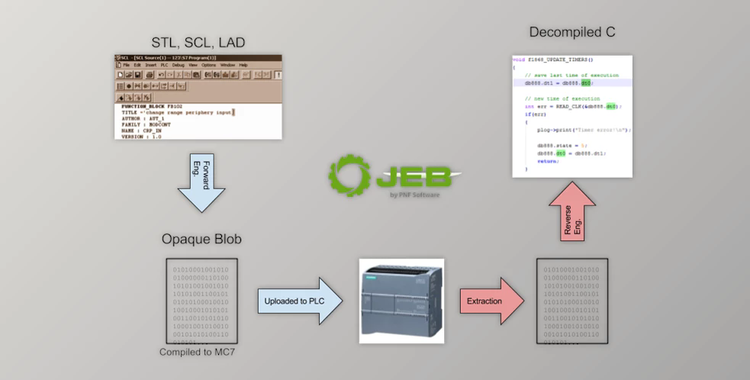
is a powerful tool designed to simplify the reverse engineering of Android applications, including both benign and malicious APKs. It significantly reduces the time needed to break down and decompile obfuscated apps, allowing users to examine Java code and debug closed-source applications quickly. With a robust user interface and a flexible backend, JEB enables refactoring operations and scripting to automate complex tasks, making it an essential tool for performing comprehensive security audits.
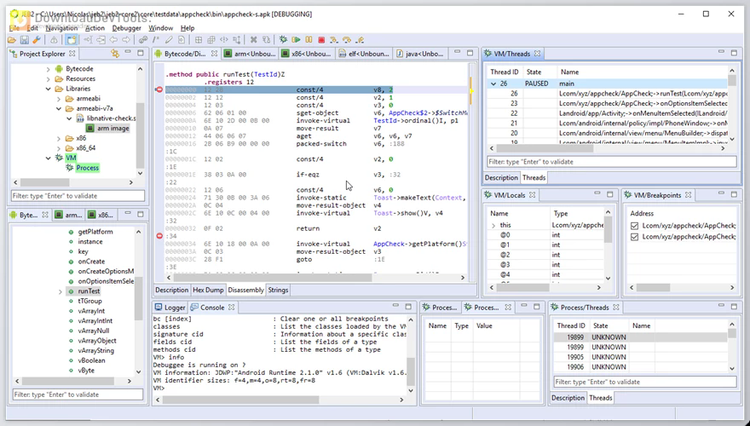
This decompiler excels at both static and dynamic analysis. It includes a Dalvik decompiler that handles multi-dex APKs and can refactor and defeat obfuscated code. Users can also reconstruct resources and obfuscated XML files. The tool supports seamless debugging of both Dalvik bytecode and native machine code (Intel, ARM), providing unmatched features for analyzing real-time applications and hooking sensitive APIs. Additionally, JEB Decompiler for Android allows for debugging of apps that do not explicitly permit it, enhancing its versatility.
JEB Decompiler for Android is highly flexible and extensible. Users can refactor, annotate, navigate, and modify the analysis output, organize highly obfuscated code, and clean decrypted content. Automation is a key feature, with an API that supports scripting in Java or Python, allowing users to write custom scripts, plugins, and even full analysis modules. This makes JEB an indispensable tool for anyone involved in reverse engineering Android applications, offering precise, real-time analysis and extensive customization options.